The HBOM Framework and the Problem of Trusting Hardware Too Much
Most security teams are comfortable talking about software supply chains now. SBOMs have become familiar, if not always loved. But hardware still sits in an awkward corner of risk discussions, half acknowledged and rarely mapped with any seriousness.
The HBOM framework exists because of that gap. Not as a silver bullet. Not as a compliance exercise. More as a way of forcing uncomfortable clarity around what hardware you actually depend on and where it can quietly fail you.
This is not a theoretical problem. Anyone who has dealt with compromised firmware, opaque OEM dependencies or ageing industrial kit knows how quickly hardware issues slide beneath the radar. The HBOM framework drags them back into view.
What the HBOM Framework Really Tries to Do
At its core, the HBOM framework is about visibility. Not perfect visibility, which is unrealistic, but enough to make informed decisions without guesswork.
It looks beyond the device label. Past the brand name. Past the procurement spreadsheet. It asks what components exist inside the hardware you rely on, who produced them, how they are maintained and how they are updated, if they are updated at all.
That sounds simple. But it rarely is.
Hardware supply chains are fragmented by design. Components move across borders, through subcontractors and between vendors that have no obligation to be transparent. The HBOM framework does not magically fix this. What it does is give security teams a structured way to document, challenge, and track those unknowns over time.
Why Hardware Still Breaks Security Models
Most security models assume hardware is static and trustworthy. Software gets patched. Configurations drift. Hardware just sits there doing its job.
That assumption is no longer true.
Modern hardware carries firmware, embedded operating systems, management interfaces and update mechanisms that behave very much like software. They just receive far less attention. The HBOM framework exists to rebalance that neglect.
There have been enough real-world incidents to prove the point. Firmware implants that survive reinstallation. Supply chain tampering that bypasses endpoint controls. Network devices running outdated embedded systems long after support ends.
These are not edge cases anymore. They are consequences of treating hardware as static.
Where the HBOM Framework Forces Hard Conversations
One of the less discussed benefits of the HBOM framework is how uncomfortable it makes procurement and architecture discussions.
Once you start documenting hardware dependencies properly, questions appear that were previously avoided. Who owns firmware patching responsibility? How long devices remain supported? Whether a cheaper alternative introduces opaque components that cannot be assessed.
The framework does not answer these questions for you. It simply makes it harder to ignore them.
That shift matters. Security decisions stop being abstract and start colliding with operational reality. Sometimes that friction is the point.
A Practical Structure You Can Visualise
This is where the HBOM framework becomes useful instead of academic. It can be broken down into a structure that teams can work with and review.
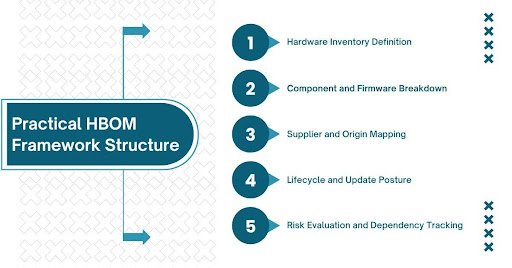
- Hardware Inventory Definition
Identify physical devices in scope, not at brand level but at model and deployment level. Context matters here. A device in a lab is not the same as one in production. - Component and Firmware Breakdown
Document known internal components, firmware versions, embedded operating systems and management interfaces. Gaps should be recorded, not hidden. - Supplier and Origin Mapping
Capture vendor, manufacturer and where possible subcomponent origins. This is rarely complete and that incompleteness is itself a risk signal. - Lifecycle and Update Posture
Understand support status, patch mechanisms, and end of life timelines. Hardware without a credible update path deserves extra scrutiny. - Risk Evaluation and Dependency Tracking
Assess how failure, compromise or obsolescence would affect business operations. Track dependencies between hardware and critical services.
Seen together, this structure exposes assumptions very fast. It also shows where effort is being wasted on low-impact assets.
Where Teams Usually Struggle
The HBOM framework sounds manageable on paper. In practice, teams struggle with scale and ownership.
No single team owns hardware risk end to end. Security, IT, OT, procurement and suppliers all hold fragments of the picture. The framework forces collaboration that many organisations are not structurally set up for.
There is also a temptation to aim for completeness. That usually backfires. A partial HBOM that is maintained well is more valuable than a perfect one that decays after six months.
The framework works best when treated as a living record, not a one-off exercise.
Conclusion
The HBOM framework is not about ticking another governance box. It is about acknowledging that hardware is no longer a neutral foundation. It carries risk, complexity and dependencies that deserve the same scrutiny as software.
Organisations that take it seriously tend to make better long-term decisions. Not because they eliminate risk, but because they understand it earlier and with fewer surprises.
This is where CyberNX can help you. Their expert professionals can help you align with security, compliance and operational goals. They can also guide you on SBOM, CBOM and HBOM generation. For teams that lack the time or internal alignment to build this alone, that external perspective often makes the difference between a framework that exists on paper and one that actually changes how hardware risk is managed.




